ekens security & law science
International Security, Counterintelligence and Countermeasures Expert, Private Detective and Strategic Partnership Collaborations.
Ekens Security and Law Science Corp. were established by the President and the (CEO) Ekens Azubuike after completion of comprehensive studies of Police Science and Law Enforcement and Protection, Cyber Security, Counterintelligence/Counter Measures, Counter-Terrorism, Digital, and Computer Forensic Investigation, Crime Scene Investigation (CSI), Criminology, Investigation on the Deep Web (TOR), Criminal Psychology, Certificates and Diplomas in Law and law-related studies, Expert Witness/Cross-Examination Expert, Diploma in Journalism, Advance Diploma in Political Ideology, Diploma in Ethical Hacker Computer Science and Technology, including comprehensive research on the twenty-first-century global insecurities and on Cyber Security, to fill the gap on the barrier on lack of adequate crime-solving technique on some agencies.
We Provide timely and accurate counterintelligence and intelligence gathering analysis against the emerging twenty-first-century global threats with cutting-edge techniques and real-world training for cyber and social media investigations.
.

Private Investigation, Counter Surveillance Against Intruder.Police Science, Law Enforcement and Protection, International Security Expert and Consultant.

We have much Experienced in Private Investigation, Criminologist, International Security, Cyber Threats, Counterterrorism, Counterintelligence Cyber Terrorism, Criminal Psychologist, Remote Monitoring Surveillance Police Science , Law Enforcement and Protection.

WE ARE SOCIAL ENGINEERING COUNTER SPECIALIST.
Social engineering range from phishing attacks where victims are tricked into providing confidential information, and vishing attacks where an urgent and official sounding voice mail convinces victims to act quickly or suffer severe consequences, or physical tailgating attacks that rely on trust to gain sometimes resulting of ransom.
We engage in elite cyber investigation, with cutting-edge techniques and real-world training for cyber and social media investigations, The Intelligence Cycle, Intelligence Collection Disciplines, Privacy and Data Protection, Social Media Intelligence, Open Source Intelligence
Social Media Intelligence & Investigations, Mobile Apps Intelligence & Investigations, Cellphone & Mobile Forensics, Digital Evidence, Social Network Searching & Monitoring, Deep Web & Darknet Investigations, Cryptocurrency Anty Exploration, Terrorism Investigations with Social Media, Legal Fundamentals.
We undertake international security and intelligence bureau services on professional surveillance and investigation, both domestic and international high-profile security advisor with legal principle requirement on competitive intelligence gathering strategies, and supply spy gadgets as legally permitted for security surveillance and remote monitoring applications, We are proud to own our 100% indigenous anti-theft anti-kidnapping tracking GPS – GPR devices and server for personal objects and vehicles monitoring to prevent takeoff function with two-way conversation for auto report position that would send the last location if the object enters into a blind area, while clients could add or changes username and password and to monitor on SOS feature, which would send an alert of geofence to the user when it reaches the restricted area, and would send an alert of movement to the user when it begins to move or over-speed alert to the user when the target moves or exceeds the restricted speed, also to send a low battery alert to the user if the battery is low and send the alert if the belt is taken off even indoor monitoring, visit our live tracking section for more details.
Whenever you make a decision to look for a private investigator or believe you might have issues with anyone that required a secondary thought. We provides professional and ethical investigation with discreet to our client. No matter how complex or sensitive of your problem. We are likely to have experienced similar over the past years of our investigative job and are in a position to assist you.
Private Investigation and Surveillance

OUR COMPREHENSIVE ETHICAL HACKING SERVICE.
We are an Ethical Hacker Specialist who protects our clients against vulnerability or servers or windows and prevents buffer overflow. cross-site scripting, IP Poisoning, Agent or Botnets, Spoofed, Flood Attack.
WHAT IS A VULNERABILITY?
A vulnerability is a weakness that can be exploited by an attacker to perform unauthorized action with a computer system, which can be simple of a weak password, injection, complicates buffer overflow
or exploit which is peace of code or junk of data or sequence of command that take advantage of vulnerability present in our computer system to cause unintended behavior or corona computer system such given unauthorized access to a system or allowing privilege escalation.
PAYLOAD: Payload is a part of a private user face that could contain malware or worm viruses that perform a malicious action deleting date sending spam or inscription dada
AUXILIARY: What does auxiliary do in Metasploit?
The Metasploit Framework includes hundreds of auxiliary modules that perform scanning, fuzzing, sniffing, and much more. Although these modules will not give you a shell, they are extremely valuable when conducting a penetration test.
WHAT EXACTLY IS THE MEANING OF AN ETHICAL KICKER?
Have in mind that Ethical Hacker is not the same as a malicious hacker, an Ethical hacker is a legal act of locating weaknesses and vulnerabilities of computer and information systems and replicating the intent and actions of malicious hackers but with a limitation of the intent of malicious hackers, this is done without a solution or with a solution at extra cost, this legally referred to as penetration testing or red teaming against Passive reconnaissance, Active reconnaissance, email harvesting, Mail Server enumeration, Network Scanning, Os Scanning, Nmap, Nexpose, Service Scan, Port Scan, General Scanner, DSN enumeration protection against our clients-server, denial of service or (D0S) in computer engineering science terminology.
POST VULNERABILITY:
What is Post vulnerability?
POST is data that is directly sent from the user in a raw manner, with no checks or validation between the user and your program. Even if you were to validate the form that should originate the data, an attacker could manually craft a request with whatever data he wants.
Note: it’s imperative to know that I am a Certified Expert in Cyber Investigations (CECI)
CECI is the most Recognized Global Expert Level Cyber Investigative Board Certification
Individuals from the FBI, CIA, USSS, NSA, DOJ, Military Intel, Fortune 500, and Law Enforcement around the world attend this incredible program each year
Certified Experts in Cyber Investigations (CECIs) are the industry’s Most Elite Cyber Investigators that are trained in advanced and state-of-the-art methodologies to identify, investigate and resolve the most complex cybercrimes known to man. They are simply the Best of the Best
The Professional Board Certification I underwent focused on enhancing skill sets as an Expert in Cyber Investigations
The Cyber Intelligence Certification I had undergone is as follows
Certified Cyber Intelligence Professional (CCIP)
Certified Counterintelligence Threat Analyst (CCTA)
Certified Organized Retail Crime Investigator (CORCI)
Certified Social Media Intelligence Analyst (SMIA)
Certified eCommerce Fraud Investigator (CEFI)
Certified Forensic HiTech Investigator (CFHI)

Ekens Azubuike, President
Ekens Security & Law Science Corp.
Providing timely and accurate counterintelligence and intelligence gathering analysis, Investigation with cutting-edge techniques and real-world training for cyber and social media investigations
- Consultants with Security Strategy Policies, Standard and Procedures Development, Advance Security Planning and strategy, Crime solving techniques, and Investigation
- Helping organizations to design, develop and deliver information on security awareness to reduce risk and satisfactory legal requirements at your organization.
- Consultant’s to help in developing a comprehensive set of security policies both nationally and internationally depends on the specific requirement of your business, consequently, our strategy would result more effectively and pass the serving of your need
- Policies to help with crime reduction in urban, cities, state, and rural hubs, also our firm help with a recommendation on current physical security and crime challenges around the globe.
- Observation and recommendations that help high-profile officials and policymakers such as an office of the residency, Ministers, office of the Senate, House committee on security matters, office of the executive governor, office of the municipal chairman
- Based on the above, EKENS SECURITY AND LAW SCIENCE has made recertification one of her primary objectives due to the routinely merging of new technology into a modern security approach around the globe
- Experts are comprised of dedicated professionals with proven experience and we believe that our clients deserve top-quality services.
- Intelligence-led services in qualified profession and readiness to serve a full spectrum of individual and corporate clients, law enforcement agencies including self-insured and insurance companies, law firms, as well as those in the private sector
CERTIFICATES AND AWARDS IN RESUME FROM THE WORLD MOST PRESTIGIOUS AND RENOWNED INSTITUTIONS
First Class Honors with Distinction: Diploma in Criminology,
First Class Honors with Distinction: Diploma in Criminal Psychologist
First Class Honors with Distinction: Diploma in Police Science and Law Enforcement and Protection
First Class Honors with Distinction: Diploma in Behavioral Psychology
First Class Honors with Distinction: Diploma in Advanced Diploma in Political Ideologies
First Class Honors with distinction: Diploma in International Convention and Maritime Law
First Class Honors with Distinction: Diploma in English Literature
First Class Honors with Distinction: Diploma in Ethical Hacking
First Class Honors with Distinction: Diploma in Legal Studies
First Class Honors with Distinction: Diploma in Journalism
Certificate of Completion: Crime Scene Investigation (CSI)
Certificate of Completion: Law for (LLB) Students Comprehensive
Certificate of Completion: Digital and Computer Forensics Investigation
Certificate of Completion: Deep Web (Tor) Investigation
Certificate of Completion: Criminal Justice
Certificate: Corporate and Business Law
Certificate: Criminal Law
Certificate: Application of human rights frameworks
International Human Rights Law and Education.
First Class Honors with Distinction: Diploma in Intellectual Property Rights and Competitive Law
Certificate: in Legal Studies Laws and Judicial System
First Class Honor’s with Distinction: Diploma in Strategic Management
Diploma in Labor Law and Statutory Compliance for Human Resources
Certificate of Completion: Expert Witness
Certificate: of attendance: In Consistency with those of Canadian Diplomacy U.N
Certificate: International Relations
Certificate of attendance: Montreal Cybersecurity Conference 2018
Certificate of Attendance: Canada East Virtual Cybersecurity Summit 2021
Certificate of Completion: Counter-Terrorism, Certificate: Counterintelligence, Cyber Terrorism, Cyber Threats.
Studied
MM SCM. in International law
MM SCM. in International Humanitarian Law
MM SCM. in International Human Rights Law
MM SCM. in International Refugee Law
MM SCM. in International Investment Law
Seeking Admission for MSc In Criminology and Criminal Psychology
With much Experienced in Police Science (Law) Enf. Private Investigation, Criminologist, International Security, Cyber Threats, Counterterrorism, Counterintelligence Cyber Terrorism, Criminal Psychologist, Remote Monitoring Surveillance.

Our Area of Expertise.
- Cyber Investigations
- The Intelligence Cycle
- Intelligence Collection Disciplines
- Privacy and Data Protection
- Social Media Intelligence
- Open Source Intelligence
- Social Media Intelligence & Investigations
- Mobile Apps Intelligence & Investigations
- Cellphone & Mobile Forensics
- Digital Evidence
- Social Network Searching & Monitoring
- Deep Web & Darknet Investigations
- Lab & Virtual Machine
- Cryptocurrency Investigation
- Terrorism Investigations of Social Media
- Legal Fundamentals
- Nanny Cameras, Hidden Cameras
- Personal injury claims
- Workers Compensation claims
- Loss prevention.
OUR SERVICES INCLUDES THE FOLLOWINGS
- Criminal and Civil Investigation
- Counterintelligence
- Countermeasures
- Due Diligence and Police Oversight
- Digital Forensic Investigation
- Social Media Surveillance and Investigation
- Cyber Investigation
- Social Media Surveillance and Investigation
- eDiscovery Services
- Detection of Police Fales Accusation Against Innocent Persons
- Evidence Discovery in Civil and Criminal Cases
- Crisis and Security Analysis
- Detection of Deficiency in Police Report Against Accused Person
- Operational Intelligence
- Security Risk and Assessment Consulting
- Anti-corruption Services
- Investigation and Intelligence Report and Analysis
- Find Person’s Current Employer

- Cyber Investigations
- The Intelligence Cycle
- Intelligence Collection Disciplines
- Privacy and Data Protection
- Social Media Intelligence
- Open Source Intelligence
- Social Media Intelligence & Investigations
- Mobile Apps Intelligence & Investigations
- Cellphone & Mobile Forensics
- Digital Evidence
- Social Network Searching & Monitoring
- Deep Web & Darknet Investigations
- Lab & Virtual Machine
- Cryptocurrency Investigation
- Terrorism Investigations of Social Media
- Legal Fundamentals

- Police science investigation and intelligent services
- Criminal justice strategies and administrator
- Security consultant on strategy policies and legal standard procedures for development
- Domestic and international high profile security strategies advisor
- Police reform and recommendations
- Advance security planning strategies advisor
- Advance crime-solving techniques
- Surveillance and database record search
- Infidelity investigation of cheating spouses and for child custody and recovery
- Missing persons / skip tracing
- Criminal and Civil Investigations
- Loss Prevention and Victim Assistance
- Cross Examinations and Countermeasures
- Pre-Employment Screenings
- Accident Scene Investigations, photography and documentation
- Undercover Operations
- Electronic Monitoring
- Tenant Screening
- Assets and Insurance Investigations.

Your 24/7 Comprehensive Cyber Remote Surveillance and Analysis
Infidelity investigation of cheating spouses for child custody and recovery
Browse our pages to gain more insight of our Services
round the clock global security strategic partnership and accurate intelligence gathering and analysis
Countering spying against surface web intruder
Social media countermeasures and counter surveillance and investigation


We are committed to delivering the highest degree of professional services.
Our Counter surveillance is a measure undertaken to prevent surveillance including convert surveillance, Our Counter surveillance includes electronic methods such as technical surveillance counter-measures, the process of detecting surveillance devices, including covert listening devices visual surveillance devices as well as counter-surveillance software to thwart unwanted cybercrime including accessing computing and mobile devices for various nefarious reasons (e.g. theft of financial, personal or corporate data or from an intruder More often than not, counter surveillance will employ a set of actions (countermeasures) that, when followed, reduce the risk of surveillance. Counter surveillance is different from convert surveillance, (inverse surveillance), as the latter does not necessarily aim to prevent or reduce surveillance.
The use of automated tools to enable mass surveillance of social media accounts is spiraling out of control. So says a new report from Freedom on the Net, which warns that nine in every 10 internet users are being actively monitored online. And where this might have been done by armies of analysts in the past, it is now automated. Advances in AI and pattern analytics have enabled billions of accounts to be watched in real-time. The report highlights the darker parts of the internet world, China, Russia, parts of the Middle East, Africa, and Southeast Asia, but it also cites examples of monitoring in the U.S. and Europe and the development of commercial tools with western government money that then end up in the hands of questionable regimes. The Cambridge Analytica scandal may have exposed the raw truth about data security and manipulation on social media, but the issue is rooted in the platforms—the potential for deriving intelligence from otherwise innocuous data. Many of the tools are new, leveraging AI and pattern analytics to map relationships between people “through link analysis,” to use natural language processing to assign meaning or attitude to social media posts,” and to mine data for information about “past, present, or future locations but Ekens Security is here to manage your social life to get you protected against the intruder.
OUR SECURITY CONSULTANTS SERVICES
- Our consultant’s help on Security Strategy Policies, Standard and Procedures Development, Advance Security Planning and strategy, Crime-solving techniques and Investigation
- We can help your organization to design, develop and deliver information on security awareness to reduces risk and satisfactory and legal requirements at your organization.
- Our consultant’s help on developing a comprehensive set of security policies both nationally and internationally depends on the specific requirement of your business, consequently, our strategy would result more effectively and pass the serving of your need
- Our policies help on crime reduction in urban, cities, state and rural hub, also our firm help for a recommendation on current physical security and crime challenges around the globe.
- Our observation and recommendation help high profile officials and policymakers such as an office of the [residency, Ministers, office of the Senate’s, House committee on security matters, office of the executive governor’s, office of the municipal chairman
- Based on the above, EKENS SECURITY AND LAW SCIENCE has made recertification one of her primary objectives due to the routinely merging of new technology in a modern security approach around the globe
- Our team of experts is comprised of dedicated professionals with proven experience which we believe that our clients deserve top-quality services.
- Our intelligence-led services are provided by our qualified professionals and are ready to serve a full spectrum of individual and corporate clients, law enforcement agencies including self-insured and insurance companies, law firms, as well as those in the private sector.
INFIDALITY INVESTIGATION
Have in mind that no one wants to believe that their partner is unfaithful. but the fact is infidelity frequently causes relationships failure, So Ekens Security and Law Science can assist you to confirm or disprove your suspicions by discreetly following your partner and collecting evidence. Pictures or video provide indisputable proof of infidelity. Finding the truth about a partner is one of the most common reasons you need to hire us If you’re in doubt, it’s important that you get your questions answered, even if the truth is hard to hear.
HIDDEN ASSETS RECOVERY
Whether a foreign corrupt politicians or governments organizations even a married couples or business partners, the importance of confirming suspicion is even greater because the information could be relevant in any court proceedings. We can work closely with your legal counsel to uncover facts and represent your interests best. In addition to searching for evidence of hidden assets, Ekens Security can help you determine any secrets that the foreign corrupt politicians or your spouse even your business partner has been keeping. We have means of locating hidden assets, bank accounts, or other clandestine behavior that threatens anti-craft agencies or your personal even in a professional relationship.

Background Checks on Business issues
Hire us to do the due diligence work before you or your company enters into an arrangement with another business, to make sure that they are as reputable or profitable as they seem? Our investigator can locate and sift through records and paperwork to uncover any potential red flags that could hold up a deal. Close major transactions with the confidence that only comes from thorough our due diligent research.
YOU MAY BE IN NEED OF ONE OF OUR SERVICES
All Kind Of Criminal Records and Background Checks

Business Background Check
You should know that Investing internationally can be very lucrative but perilous, given our wide range of different laws and customs, the Ekens Security team of Experts will help protect your investment, and ensure compliance with intricate laws that can vary wildly across international jurisdictions.
Our Investigation can vet your potential business partners by verifying the quality of their operations, authenticity of any documents, nature of any criminal history, profitability, and more. Entrusting this will give you peace of mind, and free you to focus on your business operations.

Background Investigations for Personal Matters
Ekens Security is the right firm to hire for all your background checks because you cannot simply trust that everyone applying to work for your company is honest or forthcoming with all their information. Criminal records checks are only a part of a complete background investigation. Doctored resumes and false background information put your business at risk and threaten your productivity even and damage your reputation. Whether you’re making international hires or sifting through local candidates, Ekens Security’s professional investigation will help your screening process be more effective.

Find Missing People
We are dedicated to finding your missing person anywhere at any time whether they are the victim of a crime or trying to escape some debt, or running away from a broken home; people, unfortunately, go missing. Ekens Security and Law Science are well-equipped to track down missing persons and bring them back. Aside from missing persons, If you need to initiate legal proceedings against a person or a business is our duty to know where to find them first. Increase your likelihood of getting results by hiring Ekens Security.
Free Security Advise
If you want the world to be a better place, Be security conscious at all times and treat everyone as a suspect because security is not made to be compromised at any time, you become empty when you have lapses in your security which are temporary failures of concentration of memory, or judgment on your security then your life become mare guarantee
Spying with radio shoe transmitter concealed in the heel, to monitor secret conversation

LOCATE A P DEBTOR
Our process of tracking down missing individuals or debtors. including ex-business partner, a relative, We’ll create a special strategic plan based on your situation and carry out our detective job very discreetly. With our good strategies and innovative twenty-first-century technologies, you’ll have all the information at your disposal
Identity Theft

The fact is having your identity stolen is frustrating, time-consuming, and expensive to fix. Without help, it’s hard to gather enough information to go after the people stealing from you. Ekens Security would use our resources to find out the identity of the perpetrator and create a report you can use to pursue criminal charges. If you think someone has accessed your private information and may be using it without your permission, strongly consider hiring our professional detective to counter the uncountable
Personal Injury Investigation

When it comes to worker’s compensation claim, is expensive and damaging to a business’s reputation and productivity. While accidents do happen, some employees try to cheat the system by filing bogus and fictitious claims.
You can’t afford to fall prey to someone else’s get rich quick scheme. Hire Ekens Security to confirm your employee’s injuries.
Criminal Investigation

Here is the most reason you need to hire Ekens Security and Law Science to investigate your case, Because the local police departments and their detective squads are ill-equipped to do the leg work your case requires. Certain crimes, like stalking for example, routinely go without thorough investigation as resources are diverted elsewhere., Utilizing Ekens Security professional investigators in your criminal investigation is a smart strategy, mainly because we are fully dedicated to finding you the answers you seek. We can also uncover key pieces of evidence that allow police and prosecutors to take action, rather than letting the case go cold.
Cyber Investigation

The cybercrime investigator takes the lead for investigating cyber-attacks by criminals, overseas adversaries, and terrorists. The threat from cybercriminals is serious and growing. Cyber intrusions are becoming more common, more menacing, and more advanced, As a cybercrime investigator we primarily concerned with gathering evidence from digital systems that can be used in the prosecution of internet-based, or cyberspace, criminal activity. In today’s world, many crimes include the use of the world wide web. A cybercrime investigator can be used to gather crucial evidence to help solve these crimes.
Banking Instruments Section
Ekens Global Holdings and Consolidation
Take Advantage of our Banking Instruments
Ekens Global Holdings and Consolidation is pleased to announce our new lender to our services in facilitating the issuance of our financial instruments like Letters of Credits, Bank Guarantees and POF
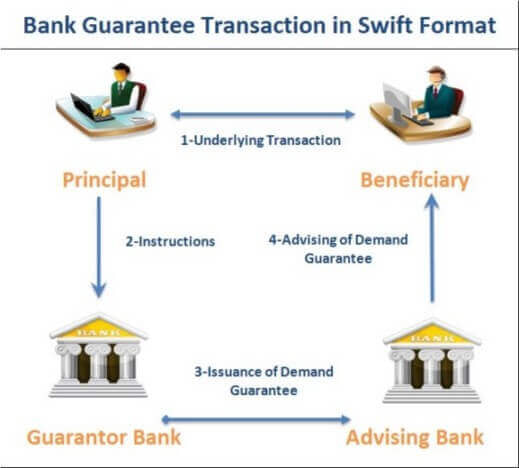
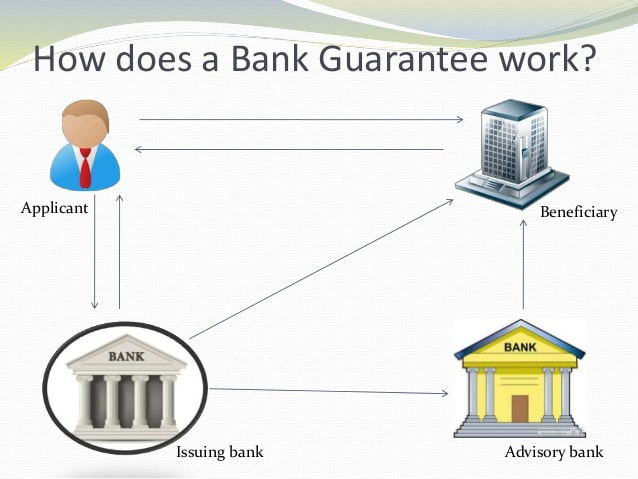
Our Banking Instruments
EKENS GLOBAL HOLDINGS AND CONSOLIDATION BANKING INSTRUMENT OFFER FOR ALL INDUSTRY – BG/SBLC/LC/POF
Our Readiness to Deliver
Ekens Global Holdings and Consolidation is ready and willing to deliver the messages of POF & RWA to your designated bank of choice. (RWA) is a document that a bank or a financial institution issues on the clients’ behalf. The document showcases the capability and intent (both financially and legally) for entering into the financial transactions.

Message from the President

take Advantage of Our Bank Guarantee for Any Project.
ekens security
counter intelligence expert
we help clients to counter police tunnel vision through
- Master observation to achieve effective situational awareness, mind to observation as much of your surroundings as possible
- Make sense out of observations to describe everything you observed.
- Challenge your environment
- Continually assess the situation
- Actively prevent fatigue
OUR MISSION
Our mission is to promote an atmosphere of partnership with all our clients, to achieve their goal in secrecy, working together with other law enforcement agencies around the globe, in strategic partnership toward the common goal of countering crimes and investigations. We are determined to enhance the overall quality of life through mutual trust, respect, and the fair and equitable enforcement of the laws while carefully safeguarding the dignity of all clients

We are dedicated to serving our global clients with less than a one-hour free consultation.
If you need a private investigator or counterintelligence, security expert? you are welcomed to send us an email in detail and we will be in touch shortly, Due to the secrecy, privacy, ethics, and confidentiality of our clients are at the top priority, considering the nature of our job, take note that visits are strictly limited appointments while meetings location may change from time to time.
CONFIDENTIALITY
Due to the secrecy, privacy, ethics and confidentiality of our clients are at the top priority, considering the nature of our job, take note that visits are strictly limited appointment while meetings location may change from time to time
Contact us
Need a private investigator or counterintelligence, security expert? email us in details and we will be in touch shortly
GIVE US A CALL
+1 (514) 446 6389
Contact us
info@ekenssecurity.com
Canada, Office
Abu Dhabi Office
Dubai, (UAE) Office
United Kingdom, Office
102
Clients
88
Returning customers
18
Academic Awards
16
Years of experience
Corporate Office:
- 1250, Rene-Levesque, Blvd. West,
- Montreal, H3B 4W8 Quebec, Canada
Contact
- info@ekenssecurity.com
- +1 (514) 446 6389
Social Contact:
Charity: Ekens Foundation

© Copyright 2021 Ekenssecurity.com All right reserved. .
